 Cloud has brought us unlimited and unmatched processing power that we could never think of a decade ago.
Cloud has brought us unlimited and unmatched processing power that we could never think of a decade ago.
Earlier, I wrote how cloud computing was actually a Dark (Cloud) Knight. And the joker was successful in showing the Gotham that even the best among us could fall. This finds a corollary in the cloud computing world.
A Look back at the Benefits: Cloud storage offers some exciting advantages. It offers “pay as you go”, with no capital outlay and no need to buy extra equipment in anticipation of future storage demands. You scale storage dynamically and pay only for what you use. But you must trust your data to the cloud and the vendor behind the service.
Are we Ready to Build up the Trust? Few mid-size or large businesses are willing to trust the cloud today, although some are experimenting. “There’s a huge amount of interest,” says an analyst at Burton Group. But, he adds, none of his firm’s Fortune 100 clients is using a cloud storage service for live data today.
Fortune 100 companies believe It’s probably wise to proceed with caution, Cloud storage today is pretty much an early-stage concept.
Aside from a few Billionaires, like Amazon and Verizon’s Online Backup and Restore service, most offerings come from small start-ups.
“It’s best suited for low-priority or low-access, low-touch kinds of applications, primarily file-based as opposed to block-based,” says a Computerworld columnist. But he says he does have clients that use services from Amazon as temporary expansion space for testbeds or marketing programs. Another company quotes “We have a lot to lose. If we’re playing, we’re only going to play with the big guys,”
Talking about Amazon’s S3 integration with educational universities, so far, has worked well. But it’s still questionable “If Amazon went down for two days, It could be a Nightmare”.
Cloud Security concerns pose Adoption Hurdle
But the attraction is real!
Reliability and Liability are still unknown in the cloud computing world: Businesses considering using cloud services will need to protect themselves against “information malpractice,” according to Drew Bartkiewicz, the VP of cyber-risk and new-media markets at the Hartford insurance company. He said that companies should stay away from cloud providers that are not open to discussing contractual, legal, privacy and compliance concerns.
Michelle Munson, co-founder and developer of Aspera thinks that reliability “is a much bigger issue than people are letting on.” She went on to say that liability and security aside, if cloud computing consolidates into too few providers, it would represent a global security concern of the highest order. Munson points to natural disasters as a primary consideration, like the Middle Eastern undersea outage in 2008 and to Google’s 2-hour May 14th outage, saying companies may not realize their exposure until after the fact. “Wait until the first 12-hour outage from a major cloud provider.” she said.
The Target Segment
The current segment under Cloud focus is nothing more than “A Storage”. The amazon and Verizon services haven’t gone much far from it. Though Google with its Apps, VOICE have taken a small step further. Still It’s merely a begining of what Cloud has to offer.
As per CloudSecurityAlliance, In the 21st century, cloud computing business models (a) challenge the presumption that a company possesses, or even controls, all of the digital business information for which the law imposes duties to preserve and produce, and (b) potentially jeopardize a company’s ability to preserve and produce required records and information. As a result, companies face substantial barriers to implementing cloud computing solutions if, as a result, their compliance capabilities and legal profiles are compromised.
Microsoft’s Azure is like a product thrown out to the market to analyze the prospects of a suite-solution- approach. We will still have to wait a while to know how well it can do.
approach. We will still have to wait a while to know how well it can do.
Th REAL power of Cloud is still yet to be seen. The processing power we would be able to leverage with Cloud services of the future will be enough to glorify the future industry.
Virtualization- The Single Immortal Warrior
Except for Virtualization, nothing else has promised a good level of security. Optimal practices in Virtualization can lead to very good results. Refer to Tips for Optimizing Virtualization across Networks.
If you are not yet convinced about power of Virtualization, consider reading Five reasons why you should consider Virtualization.
Virtualization is the single domain where had been a lot of investments and fruitfull results from Vendors like Cisco, VMWare. Cisco has innovated in field of Virtualization aware networks. On the Server Virtualization side, VMWare’s vSphere and Oracle’s Virtual Iron have seamless, secure portability of In-service Hardware switching in your data center where you no longer have to be worried about Dynamic Load sharing. thanks to Virtualization, OS is nothing but an application which can be flexibly load-balanced in the way you want to mould it to.
Portability and Inter-Operatability with Optimum Security:
Businesses using the cloud should be prepared for the worst. Yes, large cloud providers can make it easier to handle general availability issues well. But what happens when the cloud provider isn’t good enough? What are the considerations for moving applications across clouds? Or should businesses perhaps consider building a cross-cloud solution in the first place?
handle general availability issues well. But what happens when the cloud provider isn’t good enough? What are the considerations for moving applications across clouds? Or should businesses perhaps consider building a cross-cloud solution in the first place?
The ability to govern and measure enterprise risk within a company owned data center is difficult and still in the stages of maturation in most organizations. Using cloud computing resources could lead to many new unknowns in the areas of governance and enterprise risk. Online agreements and contracts are untested in a court of law and consumers have yet to taste an extended outage of services that they may someday determine is needed on a 24×7 basis. Questions still remain on the ability of user organizations to assess the risk of the provider through onsite assessments. Governance of the provider’s facilities and services could leave the user without recourse or recompense placing the risk of use squarely on the shoulders of the user. The storage and use of information that is considered sensitive by nature may be allowed but it could be unclear as to who is responsible in the event of a breach. If both the code authored by the user and the service delivered by the provider is flawed, who is responsible?
The Top concerns still left lost in the cloud as noted by “CloudsecurityAlliance” are on: How to manage each of these when there is trend shift from what we do today to what would be done in Cloud:
- Information lifecycle management
- Governance and Enterprise Risk Management
- Compliance & Audit
- General Legal
- eDiscovery
- Encryption and Key Management
- Identity and Access Management
- Storage
- Virtualization
- Application Security
- Portability & Interoperability
- Data Center Operations Management
- Incident Response, Notification, Remediation
- “Traditional” Security impact (business continuity, disaster recovery, physical security)
- Architectural Framework
Concerns still persist about loss of control over certain sensitive data. As per the Vendors, security is often as good as or better than under traditional systems, in part because providers are able to devote resources to solving security issues that many customers cannot afford.Providers typically log accesses, but accessing the audit logs themselves can be difficult or impossible. Ownership, control and access to data controlled by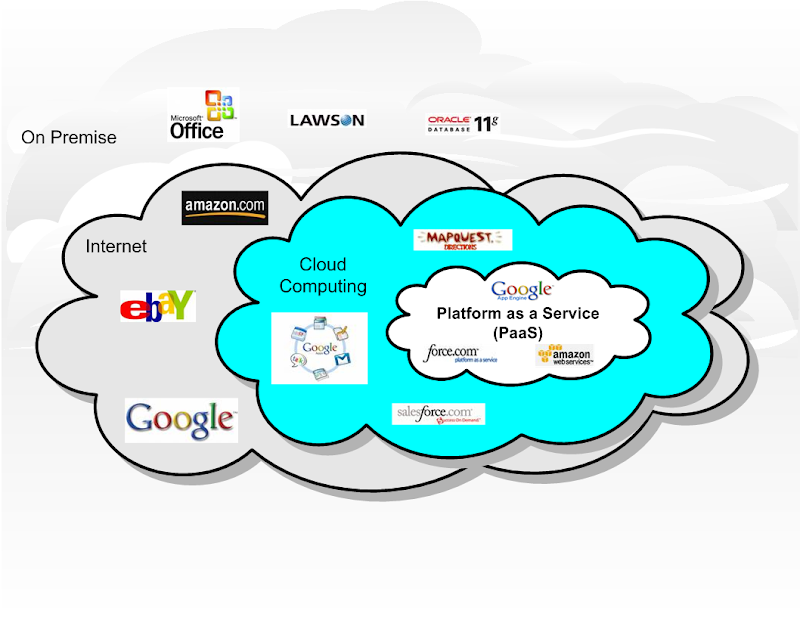 “cloud” providers may be made more difficult, just as it is sometimes difficult to gain access to “live” support with current utilities. Under the cloud paradigm, management of sensitive data is placed in the hands of cloud providers and third parties.
“cloud” providers may be made more difficult, just as it is sometimes difficult to gain access to “live” support with current utilities. Under the cloud paradigm, management of sensitive data is placed in the hands of cloud providers and third parties.
All of them need to be Re-defined to suit a new Paradigm.
Overall, the consensus is clear: The cloud’s promise of easy, elastic computing power is not enough for users with established IT organizations. That’s not to say the interest isn’t there- it is, but real-world concerns far outweigh lofty ideas at this point. Security is what Industry demands Today.
loading...
loading...
