 The end of Internet Explorer is finally here. Series of events: Google Hacking, removal of support for Google apps, several other vulnerabilities are forcing users to move to alternates.
The end of Internet Explorer is finally here. Series of events: Google Hacking, removal of support for Google apps, several other vulnerabilities are forcing users to move to alternates.
Recently, at Black Hat DC conference, a security consultant (Jorge Luis Alvarez Medina) demoed how it’s possible to exploit a flaw in Internet Explorer browser that turns your personal computer into a public file server. In other words, attacker can remotely read files on the victim’s local drive.
There are a few ways to initiate the attack, which is somewhat complex because you have to “string alot of the features together to build an attack tool,” Medina said. One method involves enticing the victim to click a link to a malicious Web site.
The flaw is said to work across all versions of Internet Explorer, and just can’t be fixed in a single shot. Medina said it doesn’t appear that the IE flaw is subject to patching because it encompasses design features related to how IE and Windows Explorer handle zone elevation, HTML code and MIME types.
Related:
As a response, Microsoft prompted a security advisory
Our investigation so far has shown that if a user is using a version of Internet Explorer that is not running in Protected Mode an attacker may be able to access files with an already known filename and location. These versions include Internet Explorer 5.01 Service Pack 4 on Microsoft Windows 2000 Service 4; Internet Explorer 6 Service Pack 1 on Microsoft Windows 2000 Service Pack 4; and Internet Explorer 6, Internet Explorer 7, and Internet Explorer 8 on supported editions of Windows XP Service Pack 2, Windows XP Service Pack 3, and Windows Server 2003 Service Pack 2. Protected Mode prevents exploitation of this vulnerability and is running by default for versions of Internet Explorer on Windows Vista, Windows Server 2008, Windows 7, and Windows Server 2008.
A workaround, according to Medina, would include setting “IE Network Protocol Lockdown,” adjusting the security level setting for the Internet and Intranet Zones to “high,” and disabling Active Scripting for the Internet and Intranet Zones with a custom setting.
Perhaps, the best that can be done is to use a different browser.
One weakness in IE is that it “doesn’t behave consistently. when accessing the same resources,” he pointed out. This exploit leverages it by “chaining the exploitation of a series of weak features.”
His dialogue with Microsoft’s security team about the exploit so far has indicated that Microsoft thinks this is not something it can fix because the flaw is so much a part of the fundamental design of the browser.
Complete Details available in this Paper [PDF]
Wake-up “User“, Are you still on IE?
We write latest in Microsoft, Windows 7, Android, Google, iPhone, Tech Guides, Open Source, Security get them all @taranfx on twitter or below:
loading...
loading...

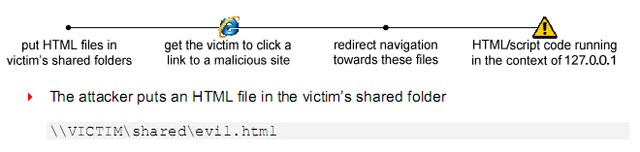
if you're able to disable the security features of the browser, put files on a computer remotely and then make it browse to a certain page you can access files provided you know the precise path to them. wowser it's wide open!
performing any one of those steps would count as a hack in its own right, if you could do all that why not just install a trojan on the pc?
this article should be more along the lines of “guy finds complicated way of using IE to share files”
loading...
loading...
LOL, just one (of many) reasons to use Firefox!
Jess
loading...
loading...
So if someone hacks into your computer they can do things that could make it easier to hack into your computer? Oh noes..
This “security flaw” is like breaking into the Whitehouse to use their stationary to fax a fake purchase order to a sex toy supplier.
loading...
loading...
Paranoia, deep destroyer!
loading...
loading...
Awesome, hopefully this will bring more users to some non microsoft flavors, preferably a browser that is still innovating like firefox, opera, chrome, or something similar!
loading...
loading...